User Authentication with Microsoft Entra ID¶
Our Microsoft authentication authority lets you log users in at the agent against Microsoft Entra ID (formerly Azure Active Directory). Our integration means that you can:
- Apply Conditional Access to user logins.
- Use any MFA mechanism supported by Azure for authentication.
- Log users in via their existing domain-joined credentials on Windows devices if you are using AD Sync.
- Audit user login events through Microsoft's tooling.
- Use your existing Security Groups to segment network access.
Azure Tenant ID¶
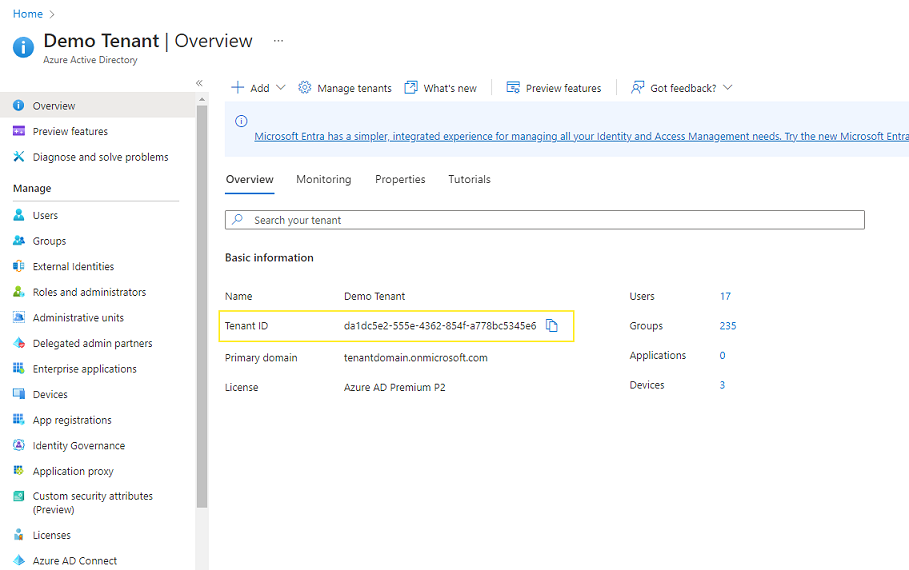
When defining your Trust Requirement, you should provide the Azure Tenant ID, which indicates which Azure tenant the authenticating user must exist in.
You can get your Tenant ID from the Azure Portal:
Security Group¶
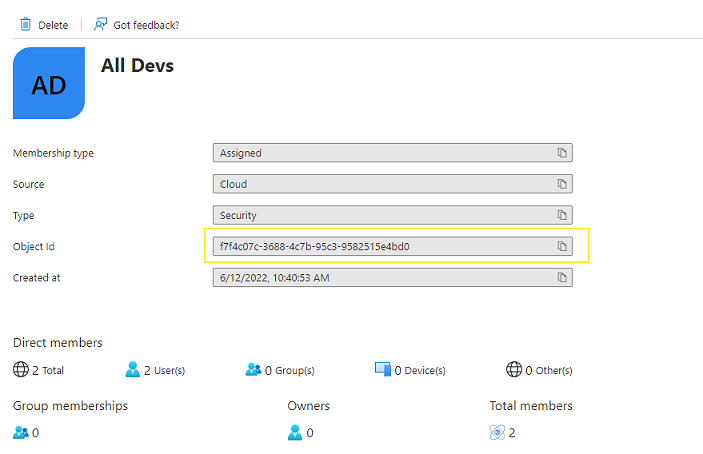
In addition to generally requiring authentication via your tenant, you can also specify an Entra ID Security Group Object Id. Users must then be a member of that security group in order to meet the trust requirement.
Using security groups, you can create finely-grained connectivity rules that map your user security assignments to the resources they can access.
The Security Group ID is the "Object ID" in Azure for that group:
Requirements¶
To use Entra ID group membership with Enclave Trust Requirements, ensure that your security groups are correctly configured in Entra ID to be compatible with third-party applications.
Many customers manage a mix of security groups, from on-premises Active Directory to Microsoft 365 Groups and native Entra ID security groups. However, not all can be used for authorisation with third-party applications.
| Group Type | Supports Third-Party Authorisations |
|---|---|
| Entra ID Security Group | Yes, can be used directly with Enclave Trust Requirements. |
| Active Directory Universal Security Group | Yes, but the groups must be synced to Entra ID using Azure AD Connect. |
| Active Directory Local/Global Group | No, must be converted to a Universal Security Group in on-premise Active Directory before syncing, or created as new Entra ID Security Group. |
| Microsoft 365 Group | No, either add the Microsoft 365 Group to an Entra ID Dynamic Membership Group, or create a mirrored Entra ID Security Group with the same members. |
Token Refresh¶
An Entra ID user may be granted system access through Azure Conditional Access or Privileged Identity Management (PIM) policies to block access from less trusted locations, force users to reauthenticate periodically or enforce device security compliance posture via InTune.
Enclave will revaluate group membership each time we receive a new access token from your Azure tenant. This happens whenever the access token expires, which is governed by Azure policy.
The default access token lifetime is between 60-90 minutes, but if needed conditional policy can be applied to the Enclave app integration in the Azure tenant to reduce the token lifespan.