User Authentication with Duo SSO¶
Our Duo SSO authentication authority lets you log users in at the agent against a Duo Single-Sign-On application in your existing Duo tenant. With this you can:
- Authenticate Enclave users with a SAML provider of your choice.
- Authenticate Enclave users with an on-premise Active Directory deployment.
- Apply Duo Push and other Duo MFA mechanisms to Enclave authentication.
Pre-requisites¶
Ensure you have set up Duo Single-Sign-On in your Duo tenant, including configuring an authentication source. Documentation on this is available at https://duo.com/docs/sso#enable-duo-single-sign-on.
Note
Duo SSO does not issue refresh tokens to us when users log in, so we cannot frequently check that a user is still valid. Because of this, user logins through Duo will expire after 20 hours and users will need to log in again.
Create a Duo Application¶
To connect your Duo instance to Enclave, you must first create an Application within Duo. Go to your admin dashboard in Duo and navigate to the Applications page, then click Protect an Application.
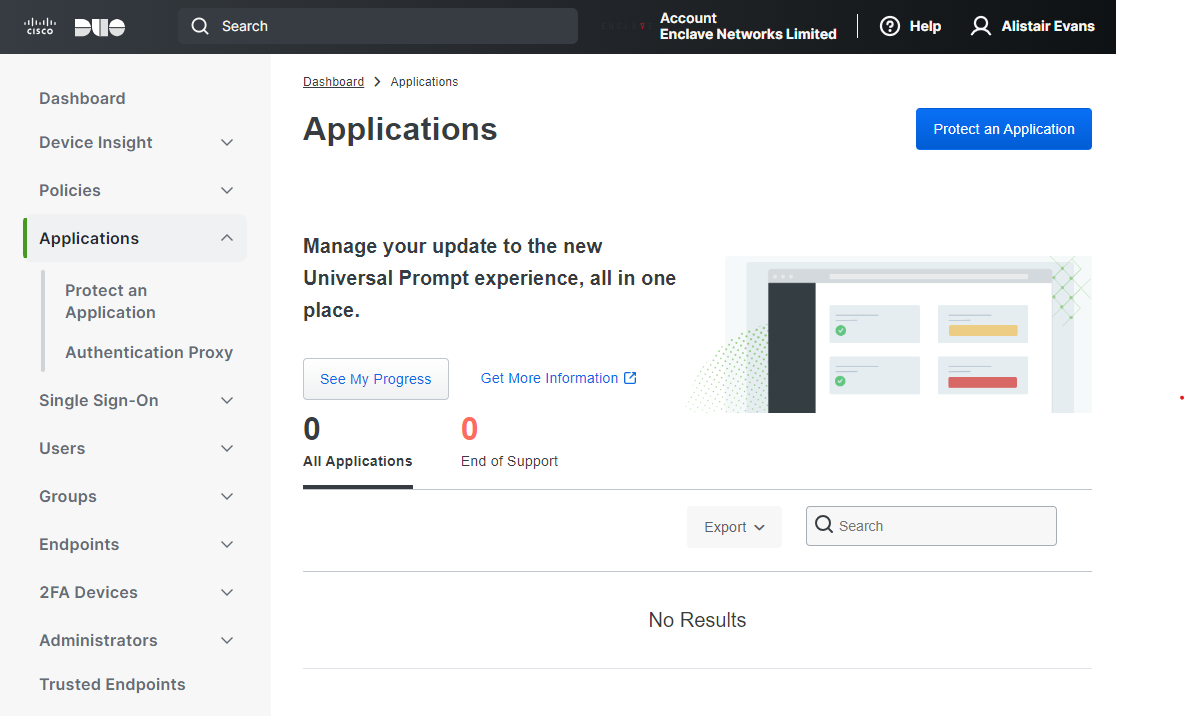
On the next page, select Generic OIDC Relying Party, then click Protect.
You'll then be shown a settings page with a Client ID and Issuer values. You'll need those to create your Enclave Trust Requirement.
On this settings page, apply the following changes:
| Grant Type | Tick Allow PKCE only authentication. |
| Sign-in redirect URLs | Specify one URL: - https://login.enclave.io/fed-callback |
| Scopes | Tick profile and email scopes. Under the profile scope, click Add Claim, then select <Username> in the IdP attribute dropdown, and set the Claim to preferred_username. |
| Name | Set to Enclave (or some other usefully identifying name) |
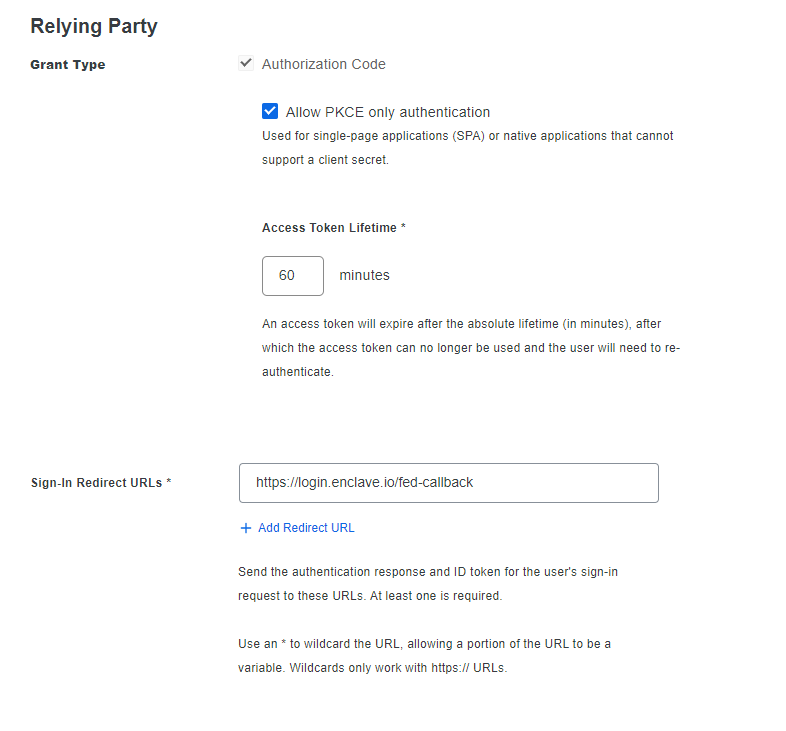
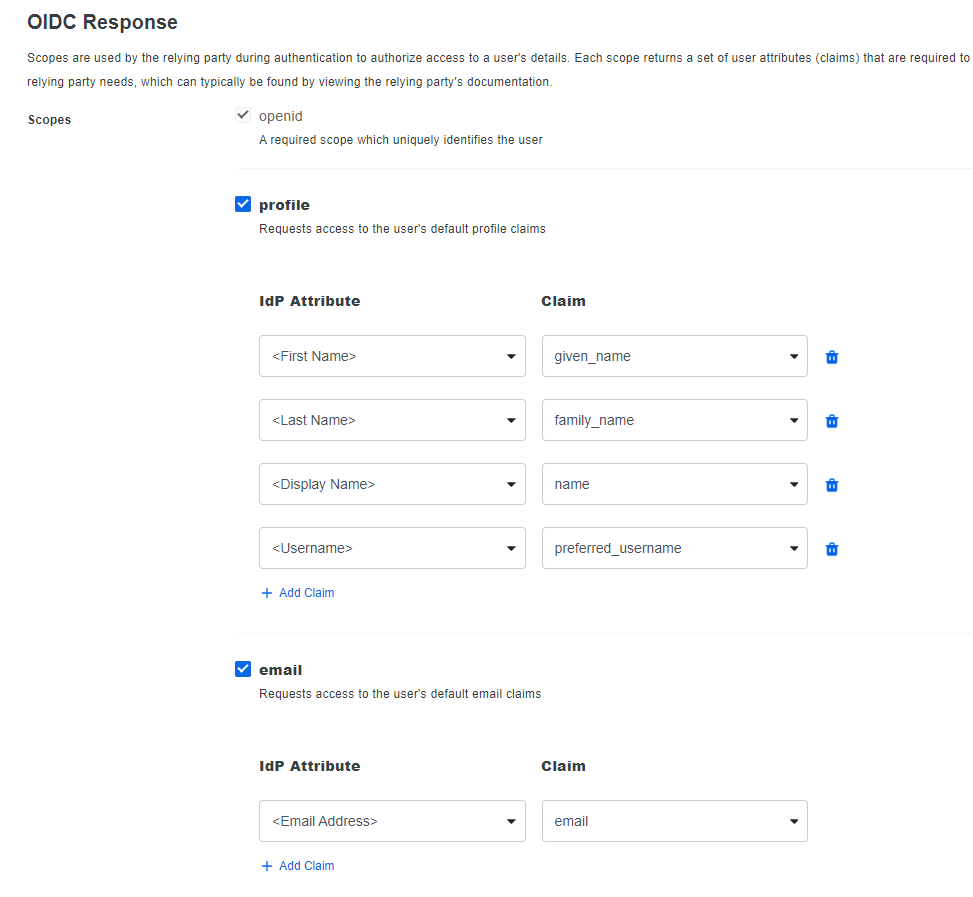
Once applied, press Save at the bottom of this page.
Create the Enclave Trust Requirement¶
Now we have all the Duo configuration set up, we can create our Enclave Trust Requirement.
When defining a new User Authentication Trust Requirement in the Enclave Portal, select Duo SSO from the Authority dropdown, and populate the fields with:
- The Duo Client ID
- The Duo Issuer
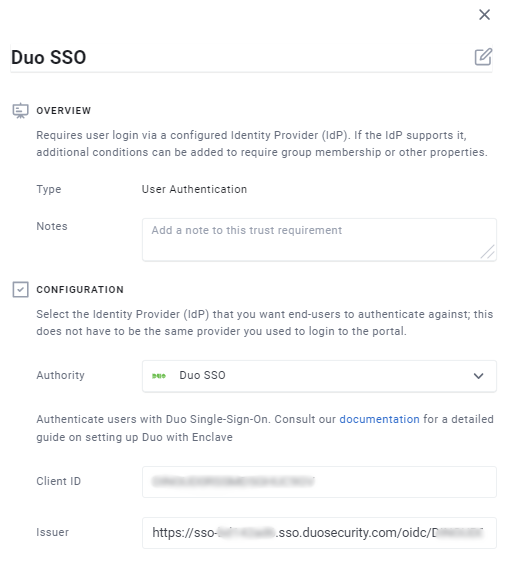
Once you press Save you can start using your Duo SSO Trust Requirement in an Enclave Policy. Your users will then be prompted to login and will be sent to your Duo tenant for authentication.