User Authentication with a Custom OIDC Provider¶
If you aren't using any of our officially supported identity providers, Enclave should still support your custom OIDC Identity Provider provided it meets the following conditions:
- Must have an Internet-facing public issuer URL; we cannot interact with an identity provider that doesn't have a public issuer endpoint.
- Must support the Authentication Code with PKCE OIDC flow.
- Must permit the "Refresh Token" grant type, allowing us to re-authenticate as a given user without requiring interaction.
Note
If you want to use a custom identity provider, but have questions about whether it would be supported, feel free to contact us at support@enclave.io.
Configuring your Provider¶
When creating an "Application" in your provider, ensure that you have enabled:
- The Authentication Code (with PKCE) flow. Other flows can be disabled.
- The refresh token grant type (sometimes referred to as the "offline_access" scope).
Ensure that the permitted Redirect URIs for the created application are:
- http://localhost:45719/
- enclave-app://agent-auth
Create the Trust Requirement¶
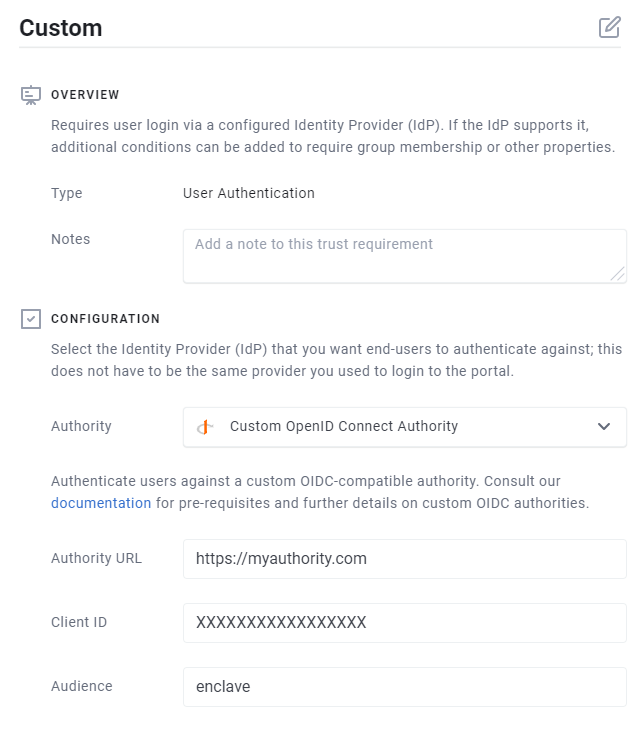
When defining a new User Authentication Trust Requirement in the Enclave Portal, select Custom OpenID Connect Authority from the Authority dropdown, and provide:
-
The Authority URL; this is the root URL of the Identity Provider, sometimes also called the Issuer. It is not the metadata URI of the identity provider. The URL should not contain a ".well-known" path value. If it does, it means you've got the wrong value.
-
The Client ID; this is a unique identifier for the Enclave application provided by your Identity Provider.
-
Optionally, an Audience. Depending on the identity provider, you may want/need to specify an audience value for the Relying Party (which is Enclave). If you do not provide a value, we will not validate the audience value in any authentication tokens we receive from the identity provider.
Once you press Save you can start using your Custom OIDC Trust Requirement in an Enclave Policy. Your users will then be prompted to login and will be sent to your identity provider for authentication.