Using Enclave with your firewall¶
Typically, Enclave is compatible with your firewall without requiring adjustments because it uses NAT traversal techniques to enable direct, peer-to-peer connectivity between enrolled systems.
However, in some cases the NAT implementation in your firewall might be a "hard" NAT, which makes it difficult to establish direct peer-to-peer connectivity, and forces Enclave to use relay servers to establish connectivity.
If you've already checked to ensure which firewall ports should be open to use Enclave, disabled TLS/HTTPs traffic inspection and continue to experience general connection issues with the Enclave platform, you may want to check our troubleshooting guide guide, or our real-time platform status monitoring pages.
If you have successfully enrolled systems which are connected to the Enclave platform, but are connecting to other peers using traffic relays, you may want to check if your firewall is listed below or configured to use a "hard" NAT mode which might prevent direct connections.
Firewall compatibility¶
| Firewall | Expected behavior | Workaround for direct connections |
|---|---|---|
| Barracuda | Relay | Open a firewall port and increase Max UDP sessions |
| CheckPoint | Connects directly | |
| Cisco | Relay | Open a firewall port |
| Fortinet | Connects directly | |
| OPNsense | Relay | Enable static NAT port mapping |
| Palo Alto Networks | Relay | Use Persistent Dynamic IP and Port |
| pfSense | Relay | Enable static NAT port mapping |
| Sophos | Connects directly | Disable traffic inspection for Enclave |
| UniFi Gateways | Relay | Allow peer-to-peer traffic |
Barracuda¶
Consider forcing Enclave to use a specific port number and then opening that firewall port to enable direct connections. This firewall does not permit administrators to modify the NAT configuration.
Also consider increasing the maximum number of supported UDP sessions allowed to prevent the firewall from restricting available UDP ports. Modify the Max UDP parameter in your firewall configuration.
Cisco¶
Consider forcing Enclave to use a specific port number and then opening that firewall port to enable direct connections. Cisco Umbrella endpoint security will not allow direct connections, and your traffic will always be relayed.
OPNsense¶
Enable static NAT port mapping.
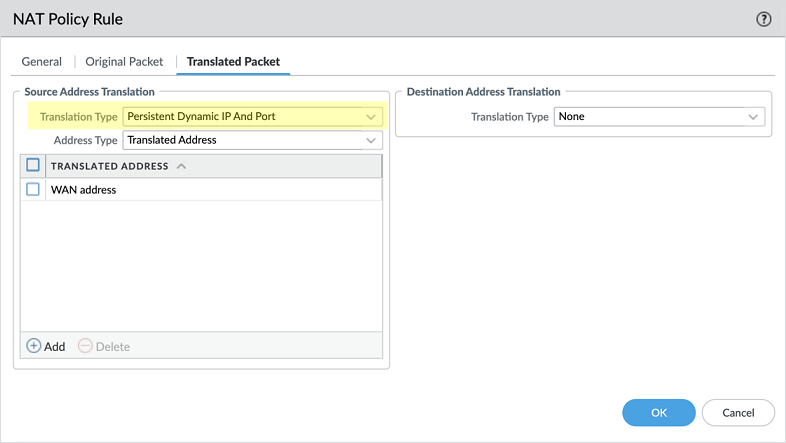
Palo Alto Networks¶
Use Persistent Dynamic IP and Port (DIPP) in the NAT Policy Rule > Translated Packet > Source Address Translation > Translation Type setting to allow Enclave to establish direct connections through the firewall.
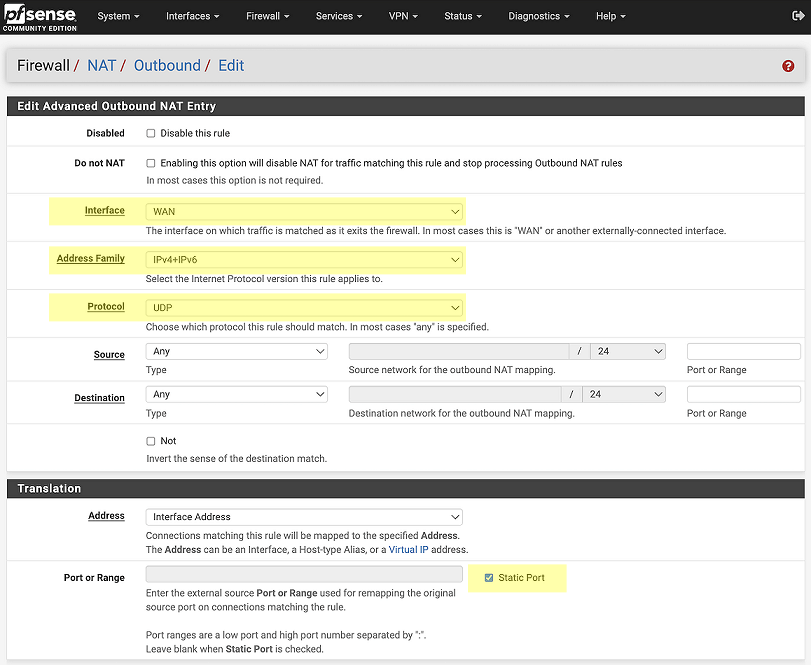
pfSense¶
Create a static NAT port mapping:
- Navigate to
Firewall > NAT, Outboundtab. - Select
Hybrid Outbound NATrule generation. - Click Save.
- Click
↑ Addto create a new NAT rule to the top of the list.
Now configure a new rule as shown:
- for Address Family select
IPv4+IPv6 - for Protocol, select
UDP - for Source, select
Any - Check
Static Portin theTranslationsection. - Restart Enclave on any systems behind the pfSence firewall to test connectivity.
Sophos¶
Systems enrolled to your Enclave tenant are expected to connect directly with default firewall settings, but general connectivity to the Enclave platform may require disabling TLS traffic inspection. To do that, follow these steps:
- Create a new
FQDN Host Groupfor the target domainsdiscover.enclave.ioandrelays.enclave.io. More information about the domains and IP addresses Enclave uses is available [here]../../kb/firewall-ports.md#enclave-platform-minimum-required-acls). - Create a new
SSL/TLS inspectionrule for Enclave. SelectDo not decrypt, with maximum compatibility modeas the destination for the new host group. - Navigate to
Rules and Policiesand then select theTraffic to WANrule group. Select and edit the#Default_Network_Policyrule to add the new host group into the exclusion list by adding it as a new item in theDestination networksfield.
See also:
Unify Gateway¶
In the UniFi gateway, go to Settings > Firewall & Security > Edit threat categories, and uncheck P2P.
Last updated April 11, 2024